50+ Sample Information Security Policys
-

College Information Security Policy
download now -

Information Security Management Policy
download now -

Bank Information Security Policy
download now -

Information Technology Security Policy
download now -

University Information Security Policy
download now -

Employees Information Security Policy
download now -

Information Security Policy Statement
download now -
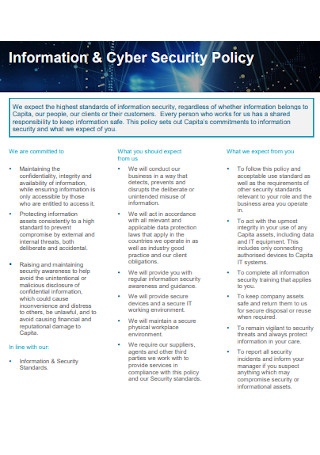
Information and Cyber Security Policy
download now -

Information Security Policy Life Cycle
download now -
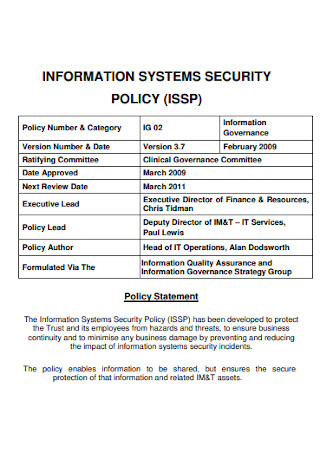
Information System Security Policy
download now -

Information Security Policy Compliance
download now -

Information Security Policy Format
download now -

I.T. Security Policy
download now -

Corporate Information Security Policy
download now -

Simple Information Security Policy
download now -
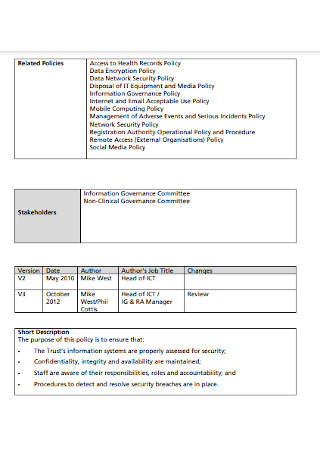
Hospital Information Security Policy
download now -

Group Information Security Policy
download now -

Quality Information Security Policy
download now -

Board Information Security Policy
download now -

IT Infrastructure Security Policy
download now -

Master Information Security Policy
download now -
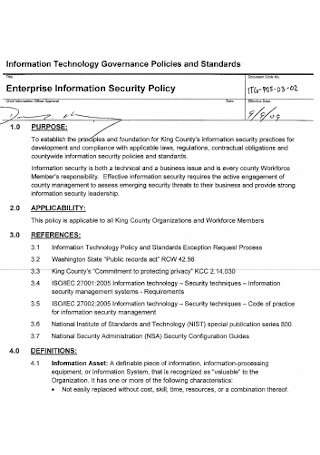
lnformation Technology Governance Policies
download now -

Global Information Security Policy
download now -

Information Security Policy Development
download now -

Information Security Governance Policy
download now -

Information and Communications Security Policy
download now -

Enterprise Information Security Policy
download now -

Data Protection and Information Security Policy
download now -

HR Information Security Policy
download now -

Information Security Review Policy
download now -
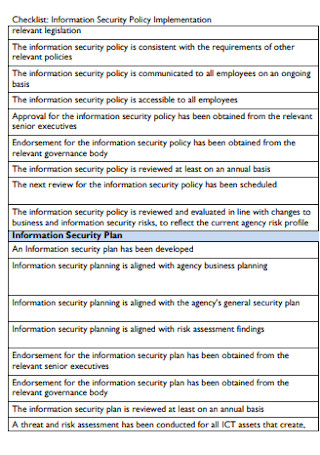
Information Security Policy Checklist
download now -

National Information Security Policy
download now -
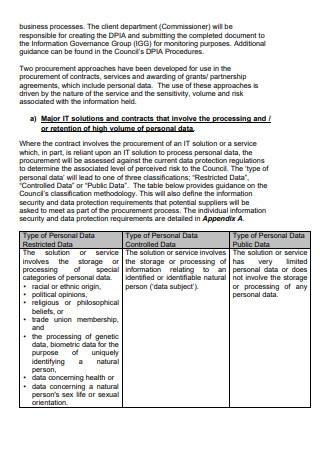
Supplier Information Security Policy
download now -

Vendor Information Security Policy
download now -

Information Security Cyber Policy
download now -

Information Security Policy Manual
download now -

Basic Policy on Information Security
download now -

Organization of Information Security Policy
download now -
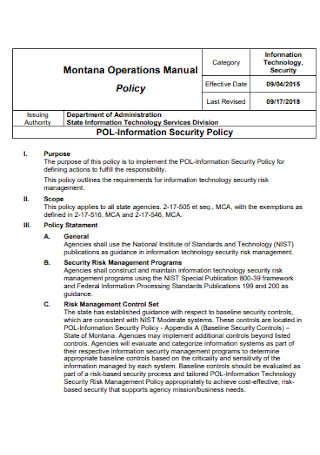
Operations Information Security Policy
download now -

Information Systems Security Policies
download now -

Digital Information Security Policy
download now -
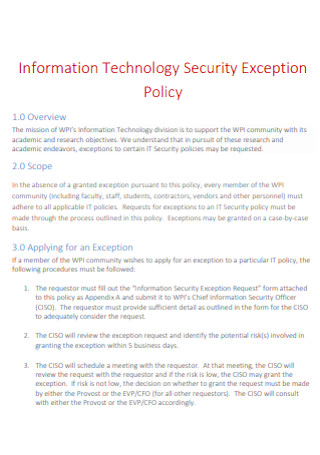
Information Technology Security Exception Policy
download now -

Information Security Program Policy
download now -

Sample Organization of Information Security
download now -

Express Information Security Policy
download now -

Information Security and Governance Policy
download now -

Information Security Policy for Users
download now -

Overarching Enterprise Information Security Policy
download now -
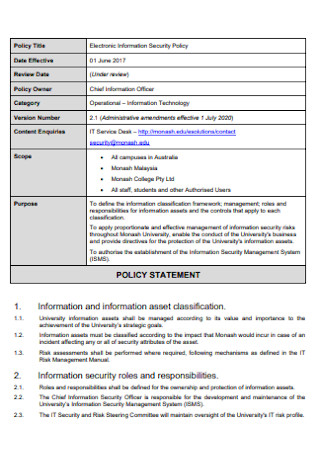
Electronic Information Security Policy
download now -
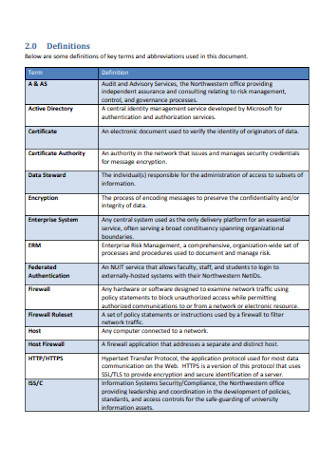
Sample Information Systems Security Policies
download now
FREE Information Security Policys s to Download
50+ Sample Information Security Policys
What Is an Information Security Policy?
Key Elements Included in an Information Security Policy
Step by Step Process in Creating an Effective Information Security Policy
FAQs
What is the difference between information security and cybersecurity?
What is the cycle of security life?
Why is an information security policy important?
What Is an Information Security Policy?
Information security policy or also known as ISP, states and defines the set of rules and procedures of a company when it comes to data. These will be the preparatory measures in case of a security breach and loss of data. It is devised to make sure that everyone who has access to the information technology resources will abide by the regulations set forth by the management. This security policy presides over all the information going in and out of the company. In several digital companies, this is an effective tool in order to fully explain the non-disclosure agreement. This is sometimes also referred as information technology security policy.
Key Elements Included in an Information Security Policy
Step by Step Process in Creating an Effective Information Security Policy
How do you write and implement this kind of sensitive document? The templates are available above. However, it is still important to know the different steps on how to write it and tips on how to implement it.
Step 1: Know the Risks
The first step in writing an information security policy is risk assessment. This can be done by retrieving past documents or by going over evaluation reports. Also, monitor the different activities of the company. This may give you an abstract idea of what complications may happen in the future.
Step 2: Do an Extensive Research
It is important to know the different security policies. This will give you an idea of what to best utilize in your company. It is also a good idea to know problems other companies are facing.
Step 3: Policies Should Abide by the Law
The document you are creating is considered sensitive. This is especially the case when you are in charge of handling valuable and personal pieces of information. Make sure that your policy will comply with the legal standards.
Step 4: Keep it Balanced
In every aspect of life, stability will always be considered. The same goes for the company. Having a high level of security and complicated policy may result in low productivity. Complex policies may become an obstruction in the business operation questionnaire. Your security policy should be matched with the level of risks you are facing.
Step 5: Incorporate Every Personnel
In creating and implementing an effective policy it would be smart that everyone is aware and has knowledge about it. Include the staff and employees in the planning process so that it would be easier for them to comprehend it when it is time to execute the plan. This will also result in unity as they can also share their point of view about the subject matter.
Step 6: The Training Process
This is a crucial step because it prepares the staff and employees for future problems. It is not enough that they have knowledge about the possible risks, it is important also that they know the plan of action when it actually occurs.
Step 7: Everyone Should Comply
Just like in a policy and procedure, for it to be considered a success, everyone should willingly comply with the plan. It is important that the document be signed and dated to make it official.
Step 8: What Will Be the Repercussions
Once again, an IT security policy is a sensitive matter. It is important that everyone understands this. In the event that the policy is violated you should be prepared. What will be the equivalent consequences for the violators? Here, it is a good idea to incorporate the elements from above. Match the consequence with what data classification they violated. This will be an effective way of determining the appropriate consequence.
Step 9: Review and Update
There will always be changes in the company. It is important to go over the security policy regularly and check if it is still effective. If not, then revise the document to be able to live up with the goal action plan of the company and the legal standards. After revision, it is required to update the staff and employees.
Step 10: Necessary Tools
The last step would be to purchase and install all the required tools and equipment in order to protect your company from possible risks. This will be an effective countermeasure tool.
Your IT security policy should be able to answer 4 important questions.
Who will get access to the data?
What will be the penalty in case of violations?
What to do and when do you need to do it?
What are the requirements in able to meet the required standards?
FAQs
What is the difference between information security and cybersecurity?
More often than not, these two terms are used in the wrong manner by accident. A lot of people often interchange them. To put it briefly, information security covers a wide array of topics of protection. Another difference is that in information security its main focus is to protect the three main objectives of security policy which is the CIA. CIA stands for confidentiality, integrity and availability of data. On the other hand, cybersecurity focuses only on one thing. The main focus of this is protecting information in the digital world or protect information from internet-based attacks.
What is the cycle of security life?
What process do security managers use in order to perform their work proficient and efficiently? They make use of a security life cycle as a model. This is to make sure that there are fewer risks and complications. This guarantees that information leaks and data breaches are greatly mitigated. This is made up of 4 fundamental steps.
1)Identify – This always comes first in all processes. The first step would always be to identify what is crucial and what needs protection. This would answer the question of what assets and resources am I supposed to protect.
2)Assess – After identifying the assets and resources you need to protect ask yourself how can you protect them. What will be the procedure in order to protect them? It is important to evaluate the potential risks that may happen in every asset you are responsible for. It is also an important step to assess the existing security measures and countermeasures.
3)Protect – Picking up from the assessment phase, after identifying the different security measures, you now have to revise and update them. Make sure that they are in line with the current policy of the company. Also, verify if they are updated to match and achieve the goal of the company. Last but not the least, make sure that they are able to comply with the legal standards.
4)Monitor – After laying the foundations of the new security system, you have to constantly monitor them to ensure that they are properly working. There will be constant changes in the company so you have to regularly update the security and make sure they are still effective.
Why is an information security policy important?
Information security policy or ISP is crucial in order to protect your company from security problem statements. These security problems usually come into being in two forms. They are namely information leak and breach of data. According to a recent research study conducted by purplesec.us, there is a 600 percent increase in cybercrimes due to the covid-19 pandemic. These malicious actors and cybercriminals usually target emails and disguised themselves as representatives for World Health Organization (WHO) and the Center for Disease Control and Prevention (CDC).
In order to prevent sensitive and valuable information to fall into the wrong hands, we have to come up with a safety measure. Nowadays it is not cowardice to be careful. According to statistica.com, 4.66 billion people in the world are actively using the internet. This is more than half of the population of the world. This means that there are billions of people that can see your information just by a click of a button. This is one of the many reasons why an information security policy is devised. By the means of this, it will limit the people who will have access to your data. It will keep sensitive pieces of information confidential.
