10+ Sample Vulnerability Assessment Report
-

Vulnerability Assessment Report Outline
download now -

Vulnerability Assessment and Adaptation Report
download now -
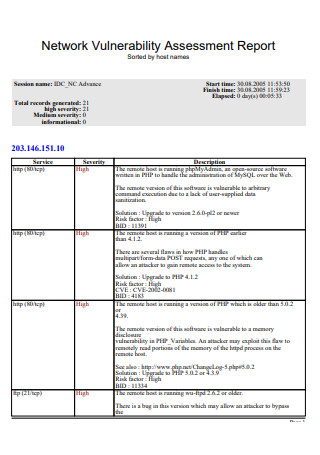
Network Vulnerability Assessment Report
download now -

Climate Vulnerability Assessment Report
download now -
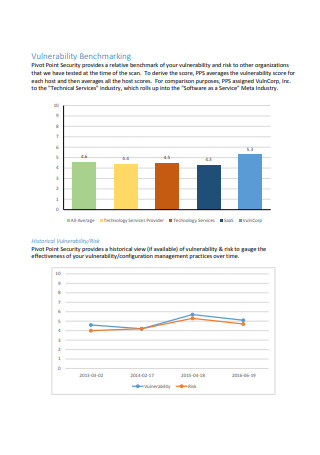
Simple Vulnerability Assessment Report
download now -
Basic Vulnerability Assessment Report
download now -

Vulnerability and Security Assessment Report
download now -

Vulnerability Assessment Report
download now -

Standard Vulnerability Assessment Report
download now -
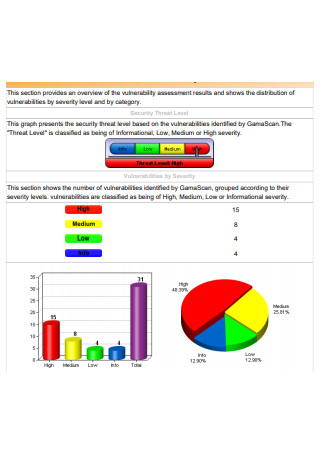
Web Vulnerability Assessment Report
download now -
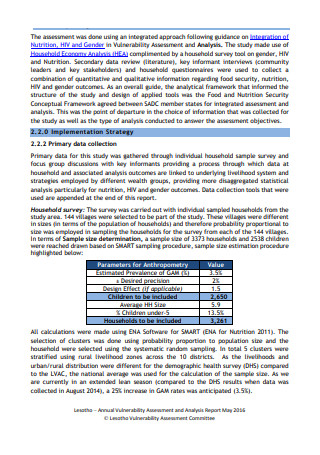
Vulnerability Assessment and Analysis Report
download now
FREE Vulnerability Assessment Report s to Download
10+ Sample Vulnerability Assessment Report
What Is a Vulnerability Assessment Report?
Types of Vulnerability
Benefits of Making a Vulnerability Assessment
How To Make a Vulnerability Assessment Report
FAQS
What Is the Distinction Between Hazard and Vulnerability?
Is Addressing a Vulnerability Necessary?
What Is the Purpose of a Vulnerability Assessment Report?
What Is a Vulnerability Assessment Report?
A vulnerability assessment report is a document that contains information about a community’s or company’s exposure and ability to protect itself from an observed threat that directly impacts them. Vulnerability is determined following a hazard assessment of a pre-existing problem that constitutes as a threat, and vulnerability is the perceived effect created by the hazard and how a community is exposed and vulnerable as a result. You can use a vulnerability assessment checklist that is tailored to a given hazard. After completing a vulnerability analysis report, one can lessen the vulnerability by developing an analysis plan that will aid in responding to a danger. By responding to the vulnerability and exposure, as well as the danger it poses to specific individuals and their security, it reduces the risk they must face once a danger has passed. Rather than relying on disaster recovery plans and dealing with the aftermath, a hazard, vulnerability, and risk assessment is far superior for preventing damage and providing protection.
According to Nancy A. Renfroe, PSP and Joseph L. Smith, PSP’s research on threat/vulnerability assessment and risk analysis, there is an amount of risk associated with various threats that all facilities must face. Natural disasters, accidents, or purposeful acts could all pose a threat. And it is the responsibility of owners or leaders to mitigate the risks posed by these dangers to the greatest extent possible. Thus, by conducting a vulnerability assessment, you are lowering the potential for harm and doing all possible to prevent or reduce a threat posed to a community by developing countermeasures and completing a vapt report.
Types of Vulnerability
There are types of vulnerability assessment in respect to potential dangers or disasters, ranging from their surroundings to someone’s social standing. And it is critical that people understand what they are exposed to in terms of the risks around them. It is necessary for them to be able to respond appropriately and safeguard their welfare. So, as an individual, you should be aware of the following types of vulnerabilities that you or everything around you are exposed to.
Benefits of Making a Vulnerability Assessment
Responding to any danger or risk often entails analyzing the vulnerability it poses to persons, society, and the environment. Although it does not simply eliminate each potential problem, it will lessen damage in a minimal but exponential manner if a response is continually modified. So, here are some benefits of creating a vulnerability scan report.
How To Make a Vulnerability Assessment Report
There are numerous approaches you could take to begin creating an assessment report. From surveys to studies. Here is a systematic vulnerability assessment guide.
Step 1: Identify the hazard/threat.
The first step is always to identify the hazard; narrowing it down would disclose its susceptibility. One must recognize the weakness for what it is, and in order to respond appropriately or comprehend its vulnerabilities, one must understand how it might be exploited. In the first place, why is it a hazard? Whose safety is being jeopardized in the first place? External risks are simply unending since there are far too many factors to consider. However, spending your time identifying what you see as damaging and potentially devastating to an ecosystem, a community, or an individual is the first step toward admitting that, yes, there are vulnerabilities that must be addressed.
Step 2: Severity
The intensity of a hazard dictates how quickly one should act in several circumstances, or even in just one case. Of course, this does not imply that low-risk dangers should be ignored, as their severity may escalate over time. Recognizing this would make it a priority to address a weakness. There are also threats that, due to their severity, necessitate prompt response. However, simply identifying it would not immediately provide that feeling of obligation and dismissing how serious it may be is plain dangerous.
Step 3: Impact
So, assessing its severity before deciding how to respond would also indicate the level of effect and damage it could cause. Because the severity would be determined by the hazard and the impact of the vulnerability. If a vulnerability is exploited or exposed to risk, the impact on the community or an individual should be highlighted in order to define its severity and the immediate worry it poses. The vulnerability’s impact would reveal negative or positive outcomes, and one may consider what suitable precautions should be taken to maximize the favorable effects and minimize the bad ones.
Step 4: Precaution
Your suggested precautions and how they minimize the problem should be included in your vulnerability assessment report. It is preferable to be specific about what your research indicates is the best course of action in response to the hazard or threat. After considering the pros and downsides, the measures should focus how to decrease risk and, to the greatest extent possible, eliminate weaknesses. However, a precaution should also be written when a vulnerability is unavoidably exploited.
Step 5: Implementation
The success of decreasing risk by recognizing vulnerabilities will be determined by when it is implemented, how it is implemented, and where it is implemented. As a result, developing a comprehensive plan for its implementation would reduce the risks it poses. Because an inefficient one may exacerbate rather than avert the threat. Implementation should take into account all external and internal factors that could lead to its failure.
FAQS
What Is the Distinction Between Hazard and Vulnerability?
The threats and dangers produced by an external factor are referred to as hazards. It could be something done on purpose, a natural occurrence, or an unavoidable consequence over time. A hazard poses a risk to a community, an ecosystem, or an individual’s safety. A vulnerability is how, because of those hazards and dangers, something or someone is affected, which could have disastrous consequences if not avoided or if no precautions are taken beforehand.
Is Addressing a Vulnerability Necessary?
If a vulnerability is not addressed, it can have devastating repercussions. Frequently, low-risk hazards appear to have no effect. However, just as a body of water becomes poisoned over time as a result of chemicals put into it, vulnerabilities that are overlooked represent the same threat to the immediate set of individual’s safeties as well as irreparable damage to its environment. So, while addressing a vulnerability is vital, recognizing it for what it is and embracing and making changes to avoid it is much better.
What Is the Purpose of a Vulnerability Assessment Report?
Being ahead of the game by identifying a hazard and its negative impact in the form of vulnerability and creating a vulnerability management report or vulnerability assessment report may help to avoid problems or reduce the harm it poses. As a result, a vulnerability assessment study can aid with proper contingency plans or action taken before a disaster occurs.
Again, vulnerability can be inherited or acquired, and it isn’t always a bad thing. It only becomes harmful and dangerous when there is a threat to one’s safety and well-being involved. And failing to fix or persistently refusing to accept a vulnerability because you regarded it as a weakness may come back to bite you when the threat has passed. So, if you’re going to write one, make sure you recognize vulnerabilities for what they are and look through printable vulnerability assessment report samples here on Sample.Net!
