8+ SAMPLE Network Security Checklist
-

Network Security Checklist
download now -
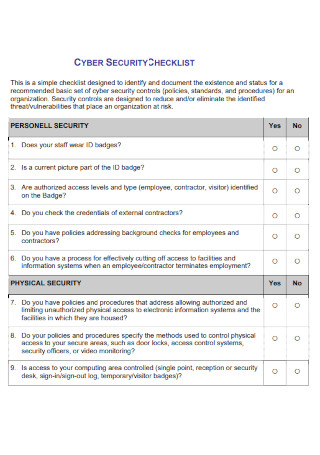
Network Cyber Security Checklist
download now -

Data and Network Security Checklist
download now -

Network Security Audit Checklist
download now -

Industrial Network Security Checklist
download now -
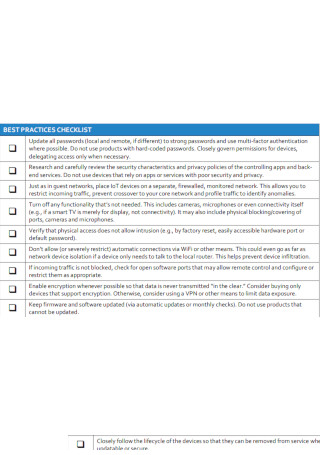
Ultimate Network Security Checklist
download now -
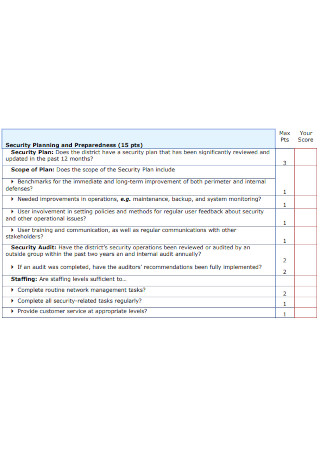
Network Security Assesment Checklist
download now -

Home Network Security Checklist
download now -

Sample Network Security Checklist
download now
FREE Network Security Checklist s to Download
8+ SAMPLE Network Security Checklist
What Is a Network Security Checklist?
Things to Consider for Network Security Planning
Examples of Network Security Mistakes
Important Items in a Network Security Checklist
How to Improve Network Security
FAQs
What is a cyberattack?
What is a network infrastructure?
What is Data Loss Prevention Software?
What Is a Network Security Checklist?
First of all, what is network security? Well, it is defined as the process of taking any kind of preventive measure, such as physical or in software form. with the purpose of protecting the network structure from all kinds of network security threats such as unauthorized access, improper disclosure, modifications, or even outright data destruction. As a result of network security, the end-users can perform their critical daily tasks with the confidence of doing so in a secure environment.
To put it simply, a network security checklist is a business document containing the list of items to be worked through whenever a workplace is undergoing a network security check or a network security audit. Having a checklist such as this one ensures that every item that needs to be checked during the audit is looked after and nothing of importance has been accidentally skipped. Having a network security checklist also greatly simplifies and streamlines the entire auditing process.
Things to Consider for Network Security Planning
Here are some pointers you can keep in mind when you do network security planning:
- Avoid Assumptions – It is essential to never, ever assume that attacks on a network will only be carried out by outsiders. Sometimes, workers from the company can even inadvertently introduce security flaws, while, in a worse case, dissatisfied or former employees can inflict significant damage.
- Improve Your Approaches – It basically means that you should resist any temptation to deal with security vulnerabilities in a partial and unsystematic method, instead, you should be dealing with them with a single, cohesive plan that puts the entire network’s best interests regarding network security at the front.
- Collaboration – This is also important as it emphasizes teamwork. Collaborate with colleagues in your company in order to establish and implement security plans that emphasize technology, training, and physical site protection utilizing technologies such as surveillance cameras.
- Return on Value – Instead of focusing on your company’s return on investment, try considering the company’s return on value instead. It is important that you consider the potential consequences of a network security breach for your company, such as lost income or customer litigation.
- Balance – As a final pointer, it is also important that you strike the right balance between a secure network and a usable one. It is no use to have a network so secure but it ends up being unusable due to the overload of security protocols in place.
Examples of Network Security Mistakes
Here are some network security mistakes that you should keep in mind:
Important Items in a Network Security Checklist
Listed below are the essential items that need to be present when you’re making a network security checklist:
How to Improve Network Security
The Internet has made our lives easier. However, it has also opened opportunities for hackers to make a mess of our lives. Here are the steps you can follow in improving your network security:
-
1. Improve Employee Awareness
This is the first method that you can employ in improving network security. Giving employees regular reminders and updates on how to protect themselves from potential attacks is an essential aspect of improving your network security. Holding regular staff training sessions or departmental meetings can prove to be a benefit whenever you include a portion on the potential of network breaches and procedures to avoid malware infection. An email reminder outlining security concerns and suggestions on a regular basis will also aid the employees in avoiding increasing network risk through irresponsible activities.
-
2. Installing a Firewall
This is another method of improving network security. A firewall helps protect your device by preventing outside parties from gaining access to sensitive information on your device. Having a firewall present on your home network will protect it from potential dangers. It will protect against unwanted access and prevent harmful communications. Most routers already include a built-in firewall. Some even include network security features such as distributed denial-of-service (DDoS) protection, web filtering, and access restrictions. After installation, be sure to enable your firewall, as it is of no use when it is just deactivated after installation. Users may forget this as some firewalls are turned off by default.
-
3. Check for Software Vulnerabilities
When performing network security audits, it is also important to check for any software vulnerabilities that may be present in the systems of your company. Almost every business now employs a number of software products from various providers. Some of these programs are compatible with both the workplace network and the Internet. As software upgrades and vulnerabilities are introduced, network administrators must keep an eye on them.
-
4. Implement Security Tasks
After checking for any software vulnerabilities, you can begin implementing security tasks. However, keep in mind that even if you have pre-planned security measures in place, you might still be a victim of a security attack. However, by adopting network monitoring software and evaluating the facts on a daily basis, you may detect or mitigate assaults before they become significant problems. You may also utilize the information to identify and close flaws in your network infrastructure.
-
5. Consider Outsourcing
Implementing security measures can be a simple or complicated task, and the size of your business has everything to do with it. Based on the scale of your company, you may not have the time or resources to install and maintain the essential procedures. If so, consider outsourcing to a third-party provider with network security expertise. They may devote themselves to the security of your company, freeing up your personnel to work on revenue-generating initiatives.
-
6. Avoid Complacency
After placing the appropriate network security measures in place, it is important that every employee knows about it and they should not feel complacent about it. One way to prevent complacency is to always document your network security policies and ensure that every employee abides by them. You will be able to make modifications to the document as needed if you examine it on a regular basis. As an added bonus, potential clients will understand that you are concerned about security – including their data.
FAQs
What is a cyberattack?
A cyberattack is defined as any type of attack that occurs mainly across a computer network or system, with the primary target of the attackers being a computer network, no matter how vulnerable or invulnerable it may seem to be. They may not be necessarily new, but however, they can come in new methods with the same old goals, which is to disable systems, steal their data, or totally compromise them. Examples of cyberattacks include ransomware, a denial-of-service attack, and phishing scams.
What is a network infrastructure?
Network infrastructure is defined as the various types of hardware and software resources of a complete network that enable network connectivity, communication, operations, and administration of a corporate network. Most businesses, such as IT setups include network infrastructure as part of their IT architecture. The whole network infrastructure is linked and may be utilized for internal, external, or both communications.
What is Data Loss Prevention Software?
DLP Software or Data Loss Prevention software refers to software and any other solutions that prevent data from being moved outside of your company network without sufficient authorization. It is a cybersecurity solution that aims to prevent breaches, data exfiltration, and data destruction from your organization’s database. You can identify and prevent data breaches through this software by monitoring the movement and usage of your data in transit, at rest, and in use.
As the network security checklist is completed during the audit, it is also important to remind the employees of your company about the impact of the network security threats that they frequently encounter. As they get familiarized with the threats, you should also train them on the methods that can be used to alleviate their impact or to totally prevent them from occurring in the first place. This is because trained employees have a greater chance of ensuring that all company data is protected. In this article, you can find different examples of a network security checklist so that you have a reference when you need to make one.
