9+ Sample Access Control Scope of Work
-

Access Control Scope of Work Template
download now -

Basic Access Control Scope of Work
download now -

Access Control Permit Application Scope of Work
download now -
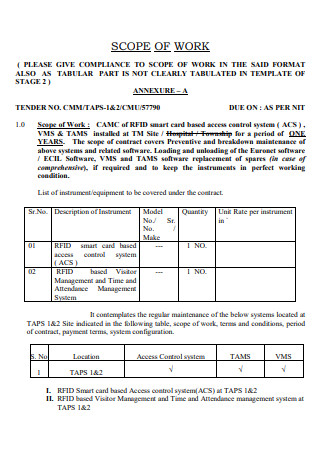
Access Control Scope of Work Example
download now -

Access Control Scope of Work in PDF
download now -

Formal Access Control Scope of Work
download now -

Standard Access Control Scope of Work
download now -
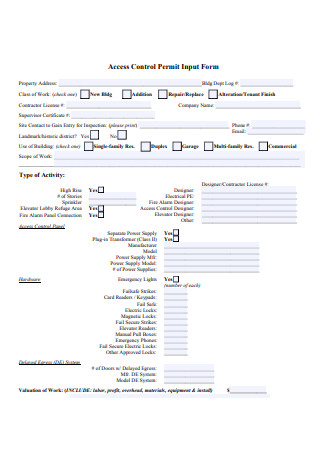
Access Control Input Scope of Work Form
download now -

Access Control System Scope of Work
download now -

Building Access Control Scope of Work
download now
FREE Access Control Scope of Work s to Download
9+ Sample Access Control Scope of Work
What is an Access Control Scope of Work?
Access Control Trends in 2023
Benefits of Access Control Systems
How to Write an Access Control Scope of Work
FAQs
What is access control work?
What does the scope of access control mean?
What are some examples of access control scope of work?
What are the benefits of using access control systems?
What are the primary functions of access control systems?
What are the four main access control models?
What are the different types of access control?
What is an Access Control Scope of Work?
An access control scope of work is a clear and well-written project scope that contains a comprehensive project scope statement and description of the installation and development of an access control system under a specific contract. It defines all key aspects of the access control system. As part of the access control proposal and access control security project plan, it plays an integral role in guiding access control specialists, security service managers, electronic security engineers, and their potential clients to have proper knowledge and understanding of the overall development and implementation process of a certain access control system and automated security equipment in every aspect of business, commerce, and industry.
Based on a 2022 statistical report, the market of access control was valued at $ 7.65 billion in 2020 and is anticipated to reach $ 11.7 billion by 2026 and continue to expand at a CAGR of 7.38% over the forecast period of 2021 to 2026. Due to the increasing global demand for access control system solutions to upgrade safety and security across many commercial establishments and residential buildings, the security and controls market changed drastically compared to the last decade. Nowadays, the latest access control technologies and systems significantly contribute to the growth in safety and security in various environments.
Thus, all types of security service professionals such as access control system administrators, IT access control specialists, security directors, access control consultants, and security managers in various firms and industries should effectively prepare an integrated access control scope of work for the continuous flow and smooth implementation of their access control system and other security services like automated equipment developed of mechanical, electronic, and optical technologies.
Access Control Trends in 2023
A survey conducted by HID Global and Security Management magazine to 473 security directors, consultants, and managers in 2019 revealed the major access control concerns at that time: integration with legacy systems, taking advantage of features in the latest technologies, protection against vulnerabilities, user convenience at entrances, and developing simplified physical access processes with digital administration. Understand the future of access control system and technology while identifying the rising trends in this field in 2023.
1. Cloud-based Access Control Systems
Many midsize and enterprise firms adopt cloud-based access control systems. The system runs in the cloud that includes email, messaging, marketing tools, IT infrastructure, sales CRMs, and website hosting. It has simplified the process of managing the access control system of a business or an organization. Cloud-based access control systems are very popular because they enable you to manage multiple sites under a single system, to have constant security updates that can be rolled immediately, and to obtain constant data backups.
2. Integrated User and Visitor Access Systems
There is an increasing number of access control providers who are opening their APIs to allow the integration of their products with others. Devices can seamlessly connect with each other by activating systems to share data and interface with third-party platforms. Managers can streamline their daily operations efficiently by selecting access control products that integrate with their business technologies. Some examples of integrated access control systems are face recognition access for users, mobile and key card access for users, PIN based temporary access, and video intercom calls for visitors.
3. Mobile Access Control Systems
A 2019 survey showed that 54% of enterprises and organizations have upgraded or will upgrade to a mobile access control system in in the next three years. This means over half of the businesses and organizations are projected in transitioning away from legacy systems in the coming years due to the emerging necessity and development of mobile access. Nowadays, access control system providers are seeking new technologies in turning smartphones into keys when unlocking or locking doors and managing access to buildings.
4. Multi-factor Authentication
People seek ultra-secure technologies because of increasing hackers, phishing attempts, scams, and other threats. Also known as two-factor authentication or 2FA, multi-factor authentication is an authentication technology that requires users to show two or more identity verification forms. It also means enabling access via use of any one of different credentials like keycard or PIN. This method of access control system has been a requirement of physical security, that’s why it becomes available to other business customers who prefer a higher level of security.
5. Biometric Access Control System
For touchless access control, biometrics like face recognition is being widely used when accessing to a building or a facility. Although is has been traditionally expensive and unapproachable, it has become a viable access control system in the COVID-19 era because it offers an easy, modern, and touchless access experience. Plus, the advances in recent years have launched biometric technology into the mainstream. It is extensively implemented for both access control and identity verification while using other technologies that include iris, palm, vein, voice, and touchless fingerprints.
Benefits of Access Control Systems
Another survey stated that 61% of IT departments set security best practices for their facilities and 55% search for new access control systems cooperatively. Additionally, the best technology advancement that would have the most impact according to 28% of respondents is integrated physical and logical access control system, especially on the improvement of the business or organization’s overall access control system.
How to Write an Access Control Scope of Work
If you don’t know or stressed where to begin and complete a scope of work or SOW for your access control system project, you need to specify any deliverables, project timelines, milestones, reports, and end products that are expected to be provided by the access control specialist. There are some easy-to-follow tips that demonstrate how to create a clear and systematic access control scope of work for security services to guide you in the preparation of your document.
Step 1: Write a General Overview of the Access Control System
Write a brief and clear general overview of the access control system that will be provided for the client. Define the work that includes all labor, equipment, materials, and services required of the contractor as specified in the contract documents. Highlight the agreement made by the contractor regarding the work, licenses, permits, inspections, and liability insurance.
Step 2: Specify Major Goals and Objectives
What are the major steps you the contractor or access control specialist need to perform to accomplish the goals of the access control project? Identify major goals and objectives to help you in attaining the goals and initiatives of the access control system. Consider the preferred outcomes to fulfill project goals and objectives. For instance, write in this part the performance, security, adaptability, and efficiency of the access control system that will be installed and implemented for the project management and security of a business or an organization.
Step 3: Explain the Project Scope
When explaining the scope of your access control system, include some proofs that your access control management team will work hand-in-hand with the clients to solve certain problems by aiming on specific areas like security and project management issues. Add the key milestones, access control system design project with anticipated timeframes of delivered tasks, reports, pricing, schedule, conclusions, and other fundamental aspects that should be executed.
Step 4: Develop an Access Control System Plan
Structure a comprehensive action plan for your access control system design project. Understand where you need to focus and analyze the development of your access control system design processes. Determine the progress of the completion of the main purpose, goals, objectives, deliverables, risks, milestones, schedule, project plan budget, and administrator or management team working practices of your access control system.
Step 5: Review and Execute the Scope of Work and Access Control System Design Plan
Read the content of your overall access control scope of work to ensure that you fully include all the crucial points in your scope of work. If you see that you overlook some sections that need more essential points, edit and revise the document right away. After proofreading and revising your document, you can now finally execute the scope of work in your access control system design plan.
FAQs
The access control work analyzes the users by authenticating different login credentials such as usernames, passwords, PINs, biometric scans, and security tokens. Most access control systems include multifactor authentication which is a process that requires multiple authentication methods to verify the identity of a user.
The scope of access control means that it enables you to restrict the rights given by a role to a particular subset of resources. It can be utilized in providing directory groups or users through permissions.
Some examples of access control scope of work are basic access control scope of work, access control permit application scope of work, formal access control scope of work, standard access control scope of work, access control input scope of work form, access control network scope of work, and building access control scope of work.
The notable benefits of using access control systems are providing freedom to employees to work at different times, keeping track of who comes and goes, creating a peaceful and safe work environment, complying with the regulations or security standards in the industry, eradicating traditional keys, increasing easy access for employees, protecting against unauthorized people, preventing against data breaches, reducing theft and accidents, and offering access to multiple buildings and locations.
The primary functions of access control systems are identification, authentication, authorization, and auditing. These systems are used to monitor the entrance and exit doors of business establishments and warehouse areas. For example, video surveillance is used for live monitoring of the location. Also, they monitor malicious activity and access and inspect and control vehicles from entering and exiting the site. For digital assets, access control systems can be used for the prevention of unauthorized access.
The four main access control models are mandatory access control (MAC), discretionary access control (DAC), role-based access control (RBAC), and rule-based access control (RBAC).
The different types of access control systems are manual access control, mechanical access control, electronic access control systems, mechatronic access control systems, and physical access control systems.
What is access control work?
What does the scope of access control mean?
What are some examples of access control scope of work?
What are the benefits of using access control systems?
What are the primary functions of access control systems?
What are the four main access control models?
What are the different types of access control?
Developing a well-coordinated access control scope of work is integral in the work of access control administrators, access control system developers, access control engineers, and access control specialists. Explain the access control design project goals and objectives and outline the access control design project tasks and processes to assist the client and the management to understand your project plan well. We have included some access control scope of work samples that you can use including formal access control project scope of work examples and access control design security services scope of work templates.
