A Security Incident Report is a critical document used to detail unexpected events or breaches affecting organizational security. It plays a vital role in recording facts, assessing damages, and…
continue reading
18+ Sample Information Security Reports
-

Information Security Incident Report
download now -
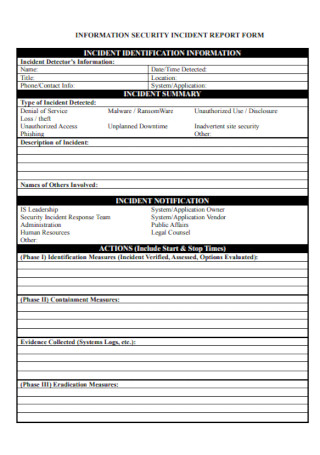
Security Information Incident Report
download now -
Information Security Report Template
download now -

Cyber Information Security Report
download now -
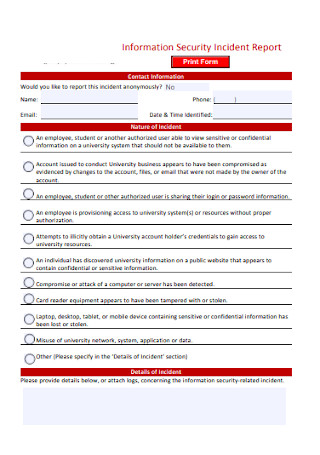
Sample Information Security Incident Report
download now -

Information Security Consultant Report
download now -
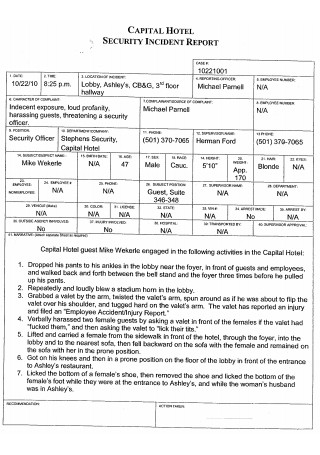
Hotel Information Security Report
download now -
Information Security Management Report
download now -

Private Information Security Report
download now -

Information Security Assessment Report
download now -
Office Information Security Report
download now -
Information Security Report Form
download now -

Information Security Audit Report
download now -
Information Security Analysis Report
download now -

Annual Information Security Report
download now -

Information Security Management Report
download now -

Information Security Incident Response and Report
download now -
Information Security Investigation Report
download now -

Simple Information Security Incident Report
download now
What is an Information Security Report?
Let’s define Information Security first. It is referring to a set of practices that are intended to protect data and secure it from unauthorized access or alterations. It is also more commonly abbreviated as infosec. The goal of information security is to ensure the utmost safety of critical and sensitive data such as login credentials, intellectual property, copyrighted property, and many others. Should an incident involving information security occur, officials are involved with reducing the impact of that particular incident, and damage limitation happens. Incidents concerning information security are to be written in an important business document known as the Information Security Report. This form contains a detailed report of the chain of events leading up to the incident.
What are the Principles of Information Security?
According to the Central Intelligence Agency, there are three main principles of Information Security. These are the following: confidentiality, integrity, and availability. It is also known as the “CIA Triad“.
The best example of the application of all three principles is that of a bank ATM. It provides confidentiality by requiring a physical card and a unique PIN code before data can be accessed and the transaction can begin. It provides integrity by ensuring that transactions made are appropriately reflected in the user’s bank account. Lastly, it provides accessibility because bank ATMs are located in a public place and are readily available even after the main bank operating hours.
What are examples of Information Security Incidents?
Every now and then, someone undetected can sneak through various security protections, causing an incident and disrupting routine activities. Here are the common examples of it:
How to Write an Information Security Report
It is vital for the people working in a company or an organization to be able to write an Information Security report, should an incident happen. Here are the steps to use as a guide:
1. Gather information.
Ask as many people as you can who saw the incident happening for details. Then gather all the necessary data, such as the date, time, and location of said incident, and the kind of information security incident that just happened. If they permit you, also include the names, the departments, and contact details of the people you’ve asked. Including their contact details enables the authorities to contact them should they have any further questions or developments regarding the incident that took place.
2. Write your personal information.
As you begin writing on the report, it is also important to write your personal information sheet in the spaces provided, including your name, contact details, your company details, and your home address. This enables the investigators to know who wrote the information security report, and also enables them to contact you for further information, or to ask for clarification should they find any inconsistencies in your report.
3. Write down the information gathered.
This is where you write the events that took place. You should remember to stick to the facts of the incidents, and never, ever include your own opinions. You should only write the facts that you are 100% sure it took place. You can also write down all the information that you have gathered from the people you’ve asked from. Also, remember to use as little technical jargon as possible. You should also format the report properly, and avoid writing a very long paragraph so that your report is easier to read. You can also attach files and photos to the information security report, to make it easier for the authorities. You can also include here a blank timeline of how the events unfolded. In writing the incident, you can remember the 5 Ws (What, Where, Why, Who, When) and 1 H (How) to make the report more authentic and credible.
4. Verify the form.
Once the report writing is finished, it is important to double-check what you’ve written in your report for missing information and facts, story inconsistencies, and grammatical errors. Make sure that all the events that you’ve written match what actually happened, and all the facts, names, and dates that you’ve listed down are factual. Also, verify that the supporting files and photos attached match the description of your report. This is your opportunity to polish your written report because any unseen typographical error can be detrimental to the progress of the investigation and may change its outcome.
5. Submit the report to the intended recipient.
Once you’ve double-checked the information security report you’ve written, and you’re confident that everything in the report is true and correct, it is now time to submit your report to the investigator, to the authorities, or whoever the intended recipient is so they can begin their investigation and provide their appropriate recommendation report and feedback. It is also important that you should submit the final report securely, using a method agreed upon by both parties. Be sure to have your lines ready in case they contact you during the investigation period.
FAQs
Is there a difference between information security and cybersecurity?
Yes, there is. Cybersecurity is defined as the protection of internet-connected systems from cyber threats. It is a broader practice of defending assets from an attack. Meanwhile, information security covers the tools and refers to the set of practices of keeping data secure from unauthorized access. Information security is a specific discipline under cybersecurity.
What is a cyberattack?
It refers to a method used by an individual hacker or a group of hackers to compromise a computer system, by modifying, encrypting, leaking, or destroying the data stored inside it. This is due to cybersecurity proposal system failure. Most cyberattacks are opportunistic, with the attackers simply detecting various vulnerabilities inside a system and exploiting them.
How many types of information security attacks are there?
There are two of them, namely active attacks and passive attacks. An active information security attack involves altering an intercepted message. These attacks are generally much more difficult to prevent. In a passive attack, however, the hacker monitors a target system and illegally copies information without detection and without altering the information. These kinds of attacks are much easier to prevent with strong security measures.
Learning all about information security and writing a corresponding report form is a vital skill to learn for any employee working in a company or organization that deals with this area of expertise. The templates provided above can certainly be used as a guide should one have difficulties in making it.

