21+ SAMPLE Security Assessment Proposal
-

Information Security Assessment Proposal
download now -

Physical Security Assessment Proposal
download now -

Security Assessment And Design Service Proposal
download now -

CyberSecurity Assessment Proposal
download now -

Security And Emergency Response Assessment Proposal
download now -

Optional Security Assessment Proposal
download now -

Request Proposal for Application Security Assessment
download now -
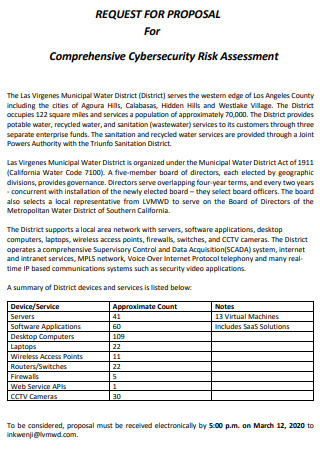
Security Risk Assessment Proposal
download now -
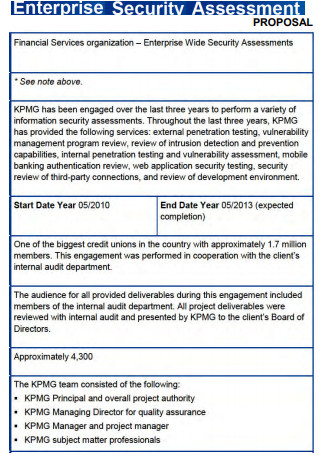
Enterprise Security Assessment Proposal
download now -

IT Security Assessment Proposal
download now -

Sample CyberSecurity Assessment Proposal
download now -

Formal Security Assessment Proposal
download now -
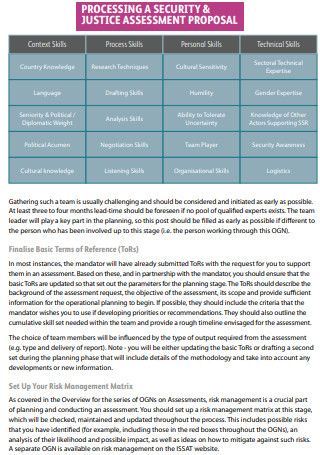
Security And Justice Assessment Proposal
download now -

Printable Security Assessment Proposal
download now -

Risk Analysis and Security Assessment Services Proposal
download now -

Security Financial Assessment Proposal
download now -

Security Third Party Assessment Proposal
download now -

Security Assessment And Testing Proposal
download now -

Security Audit Assessment Proposal
download now -

Privacy and Security Risk Assessment Proposal
download now -
Proposal for Security Assessment of Trust zone
download now -

Security Penestration Testing Assessment Proposal
download now
What Is a Security Assessment?
Security assessments are periodic exercises that examine the security preparedness of an organization. In addition to identifying weaknesses in your IT systems and business processes, they also offer countermeasures to reduce the likelihood of further attacks. In addition to ensuring that your systems and policies are up-to-date, security audits help keep your systems and procedures current. You can undertake security assessments internally with your IT team’s assistance or with an external assessor’s aid. Despite being more expensive, third-party security evaluations are beneficial if an internal preliminary assessment finds severe security weaknesses or if you lack a specialized team of IT professionals with competence in this area. According to statistics, sixteen percent of small businesses undertook a security audit only after a breach.
Benefits of Security Assessment
The digitization of information in the modern healthcare industry has enhanced services and patient care delivery, but it has also created some significant side effects: cyberattacks and data breaches. The IT departments of today must be diligent in finding network weaknesses before being targeted by cybercriminals. The necessity of conducting routine security audits for your firm is explained here.
How to Conduct a Security Risk Assessment
You can do two types of risk assessments, but the most efficient method is to combine elements of both. Both of these categories have importance, and both will enable you to convey risk to various types of individuals. For instance, your legal and finance teams will likely be most interested in the figures. Still, your operations teams, such as sales and customer service, will be concerned with how a security incident will influence their operations and efficiency. Following these steps will enable you to conduct a basic information security risk assessment and equip you with the necessary resources to establish a standardized method for identifying essential business threats.
Step 1: Document your information assets
A risk assessment’s initial phase is compiling an exhaustive inventory of your informational assets. It is essential to note that different roles and departments will have different viewpoints on the most valuable assets, so you should solicit advice from multiple sources. For salespeople, your company’s CRM may be the most significant information asset, IT’s servers are likely a higher priority, and HR’s most important asset is sensitive employee information. After placing all your information assets and essential stakeholders across all departments, you must rank these data assets based on their sensitivity level and strategic value to the firm. You must speak with all primary departmental systems administrators to obtain accurate and comprehensive information.
Step 2: Identify dangers
When considering dangers to data security, hackers are typically the first to come to mind. However, there are other threats to your business’s information security. This list of 2019 data breaches demonstrates that while hackers exploiting vulnerabilities in a company’s firewalls or website security systems has been a prevalent tactic, various threats contributed to data breaches in 2019. When establishing a list of all the various hazards your firm confronts, you must account for a variety of distinct threats kinds. In addition to harmful human interference, you must also account for accidental human interference, such as employees mistakenly deleting information or clicking on a malware link. Depending on the quality of your hardware and data systems, you may also need to consider the possibility of system failure. Lastly, natural calamities and power outages can cause just as much devastation as humans, so you must also account for such dangers. After this phase, you should have a comprehensive list of the threats to your assets.
Step 3: Identify weaknesses
A vulnerability is a weakness in your strategy or operations that could result in an information security breach. For instance, if your organization saves customers’ credit card information without encrypting it or testing the encryption process to ensure it’s working correctly, this represents a considerable security risk. Permitting weak passwords, failing to install the latest security patches on software, and failing to restrict user access to sensitive information are actions that leave your company’s sensitive data open to attack. During the coronavirus health crisis, you may also be vulnerable to a lack of personnel. Security controls are in danger of not being implemented because IT security personnel are working remotely or are ill.
Step 4: Analyze internal controls
Following the identification of system and process vulnerabilities, the next phase is to develop controls to mitigate or eliminate the vulnerabilities and threats. This could be controlled to eradicate the exposure or to address risks that cannot be stopped. Technical controls include computer software, encryption, and tools for detecting hackers and other intrusions. Non-technical controls include security rules and physical controls. Controls can also be classified as preventive or investigator controls, meaning they either prevent, detect, or inform you when an incident occurs. Developing adequate controls calls for experience and expertise. If your company lacks in-house security and compliance subject matter specialists, it is imperative to seek help from professional services businesses with extensive experience addressing IT security challenges.
Step 5: Determine the probability that an event will occur
Using the assets, the threats those assets face, and the policies in place to manage those threats, you can now classify the likelihood that each of the discovered vulnerabilities will be exploited. Numerous organizations use high, medium, and low categories to represent the probability of a risk occurring. Consequently, if a business-critical application is out-of-date and there is no mechanism for frequently checking for updates and installing them, the likelihood of an incident affecting that system is likely to be significant. On the other hand, if you handle a large volume of personal health information, have automated methods for encrypting and anonymizing it, and periodically test and inspect the efficacy of these systems, the risk of an incident is minimal. You must leverage your understanding of your organization’s vulnerabilities and control implementation to make this judgment.
Step 6: Determine the effect a threat would have
This stage is known as impact analysis, and it must be conducted for each identified vulnerability and threat, regardless of their likelihood. To understand it completely, you should analyze an incident’s quantitative and qualitative effects. You can assess if danger would have a high, medium, or low impact on your company based on the three characteristics listed above. This effect analysis and the likelihood of an incident will help you prioritize these risks in the next stage.
Step 7: Prioritize your information security risks
Prioritizing your security risks can help you establish which ones require immediate action, where you should concentrate your time and resources, and which can wait. For this phase, it may be helpful to create a simple risk matrix that allows you to plot the information you already have about each identified vulnerability/threat pair on the matrix. Risks likely to occur and have severe repercussions would be mapped as a high priority. In contrast, risks that are unlikely to occur and would have little repercussions would be mapped as the lowest priority, with all other risks falling somewhere between. Your risk matrix can be as simple or sophisticated as you deem helpful. If you are a large firm with significant risks competing for your time and attention, a 55-risk matrix will likely be beneficial; smaller organizations with fewer hazards to prioritize can probably use a 33 matrix with the same effect.
FAQs
What is a proposal letter?
A proposal letter is a formal letter to submit a bid and conclude a commercial transaction. A proposal may be for a long-term or short-term involvement. This letter may propose an ongoing commercial relationship or offer one’s services for an upcoming event.
What is a security proposal?
The security company gives a possible client who needs security services a document called a “security proposal.” The proposal should be complete, creative, and include all critical information about the organization’s products and services to get a client.
What is risk in security?
Risk is the possibility of assets or data being lost, damaged, or destroyed due to a cyber attack. A threat is a process that increases the probability of a harmful occurrence, such as exploiting a vulnerability. And exposure is a flaw in your infrastructure, networks, or apps that exposes you to possible risks. When a threat exploits a weakness in your IT infrastructure, web, or apps, it can put your assets, data, and business in danger.
It’s a little hard to make this proposal, especially since it requires planning the correct terms and conditions to reach goals and objectives. But doing this to make sure your cyber systems are safe and to teach your employees what to do if security is broken is a great thing a company could do for its employees. With this, you can start by making your proposal and giving it to the right people.
